Here you will find a selection
on common questions about software and books.
The EPUB format has become established as an open standard for digital books. It is considered to be the successor of the older formats OEB and OEBPS. EPUB files can be viewed and read using readers such as the Amazon Kindle, Sony Reader or Tolino, etc. In addition, there are a lot of apps that are available for both Android and iOS. On Windows, maxOS and Linux you can use the open source program Calibre. With Calibre, you can also convert EPUBs to other formats, such as PDF or the MOBI format.
CAD stands for Computer Aided Design. The user will be supported in his work by autmatized processes. The most well-known CAD program is likely to be AutoDesk CAD. Other well-known programs include AutoDesk Inventor, Catia and SolidWorks from Dassault Systems, NX and Solid Edge from Siemens, just to name a few. There are also free CAD programs available under different licenses. The best known are HeeksCAD (BSD), FreeCAD (OpenSource) and QCAD (OpenSource).
YES – As a free alternative, the open source program Apache OpenOffice has proven itself for many years. OpenOffice offers, like Microsoft Office various programs for word processing, spreadsheet, presentation and a database program. In addition, it includes a formula editor and a drawing program. OpenOffice is available for all major operating systems (Windows, MacOS X, Linux). With its compatibility with the widely used MS Office formats (.DOC, .XLS, .PPT, .MDB), data exchange with users of other office suites is no problem.
Apache OpenOffice can be downloaded for free via the following link https://www.openoffice.org/download/index.html
For beginners and changers we recommend the book (only in german) OpenOffice 4 für Ein- und Umsteiger by Jörg Schieb
Someday It happens to every user! By accident you delete files from your hard disk, memory card or some malware infected parts of your system. With data recovery software you can restore all or most of the data. What happens “inside” the software and how does it work?
When you delete a file or start a quick format on your memory card the operating system does not physically delete the data, it deletes the pointer or address where the data has been stored. As long as you don’t overwrite those data because the storage is slowly full, the original (deleted) data will remain at its position.
The data recovery software uses different methods to restore your data. The easy and fast way is to restore the table of content – meaning the pointers and address to the data on the hard disk or memory card. When you recognise the missing / deleted files within a short period and did not store much data after the event of deleting, your chances are quite high that most of your files will be fully recovered.
In case you discover that files are missing after a longer period and have been working with the storage (hard drive / memory) saving new files, photos or other data, the process of restoring will be more challenging. For these cases you need a sophisticated solution like ” EaseUS Data Recovery Wizard”
EaseUS Data Recovery searches for special pattern on the storage. Every file type (pictures, word documents, excel files etc) have a certain file construction. The data recovery software scans the complete disk to find these patterns and displays a list of files or file fragments that can be restored. This process takes a while depending on the speed and size of your disk.
After the search of deleted files is completed you are displayed a list of files that could be saved and restored. Often it shows different versions of the same file. Working on e.g. a word document and saving it a couple of times produces different versions of the same document. Also you only “see” one version the text editor produces varies duplicates. Always try to restore the newest version first.
Even the best data recovery software can only restore files that are still “physical” on the disk. When your disk is very full and you have worked a lot with your device before you discovered the deleted files, the results can be very poor. EaseUS Data Recovery tries even to recover fragments of your files. Receiving back at least some of the text, sheet or parts of a photo is in many situations better then loosing everything.
Best practise is to backup the entire disk or important folders automatically within a certain period of time. EaseUS Todo Backup Home helps you to easily save your data and save you a lot of time too.
What is fileless attack?
Fileless malware attacks are also referred to as fileless attacks. They are sometimes also referred to as non-malware attacks, although the term
is not technically accurate.
Unlike file-based attacks, fileless malware attacks do not download malicious files or write content to disk. Attackers exploit application
vulnerabilities to inject code directly into the memory space of an existing application. They can also leverage trusted office applications or
administration tools native to Windows OS, such as PowerShell or Windows Management Instrumentation (WMI), to run scripts and load
malicious code directly into memory. Like all attacks, the goal is to gain control of computers to achieve the attacker’s goal, such as destruction,
distortion (ransomware), data/credential theft, or additional attacks.
How to Stop Fileless Attacks at Pre-execution
At Bitdefender, we challenge ourselves to protect our customers against the full spectrum of threats: file-based and fileless malware.
As in the example illustrated above, a phishing email containing a link takes the user to an exploit-hosting site. The browser exploit triggers
PowerShell running command line (script), then PowerShell follows the instructions to download additional script (typically a larger command
line) from a remote site. The larger command line contains fileless malware that is assembled and run directly in memory.
In a second example, a user may receive a phishing email with a .doc attachment containing a macro. If the user enables the macro, essentially
a VBA script, it triggers the PowerShell script that downloads additional scripts containing fileless malware code from a remote location. It then
injects that malicious code into the memory space of a vulnerable application.
Bitdefender has recently released an update that improves your privacy protection.
Die neueste Version von Bitdefender now offers “Anti-Tracker”, a browser extension that lets you know what information websites collect about you.
Unfortunately, there is no such thing as anonymity on the web.
You leave a digital footprint every time you visit a website. With every click, data about you and your online habits is collected and stored’.
Examples: A search on the topic of ‘fitness’ is enough for you to be offered a membership for a fitness club at every corner of the internet. Have you ever wondered why the car ad you clicked on suddenly appears everywhere? Or why the airline tickets are suddenly more expensive after a quick glance at them?
Anti-Tracker helps you!
Once activated, Anti-Tracker displays a list of trackers embedded in the pages you visit. Even better: with its help, you can then switch off these trackers and continue surfing without leaving traces everywhere. The extension is initially available for Chrome, Internet Explorer and Firefox.
If you haven’t received the update yet, don’t worry: it won’t be long now. What’s more, it is completely free of charge for you.
According to a study by the Aberdeen Group , companies that use video on their website receive 66% more qualified visitors. In addition, these companies achieve 54% higher brand awareness.
There are numerous agencies that create image films or produce product videos. Although these films and videos meet professional standards, they are usually very sterile and thus extremely boring for the target group.
One achieves a multiple of attention if the needs of the specific target group are addressed directly and honestly. A product manager from one’s own company is not necessarily trained to appear confidently in front of the camera, but he/she can convey the enthusiasm for the offered service or product more honestly and competently than a professional actor who only reads out a given text.
The production of short videos does not have to be expensive. With a few good video templates and easy-to-use video editing software, results are achieved that delight customers and interested parties alike
A few tips on how to produce interesting videos yourself:
- Think about your customers
Explanatory videos on the products and the services offered can be created by the product managers in the best possible way. You know the question your customers are asking, so why not create short explanatory videos on this? - Brevity is the key – videos should be short and interesting.
No explanatory video should be more than 10 – 15 minutes long. Get to the heart of the matter, don’t ramble on too much and keep the viewer in suspense.4 - On which platform should the videos be published?
If you have your own server, you will have to pay for maintenance as well as the costs of the server. In addition, the videos are only seen by visitors to your own website. To achieve more reach, it is better to publish the videos on a video platform such as YouTube, Vimeo or Facebook. It is important to give the videos good “tags”, i.e. keywords, so that they are also displayed in corresponding search queries. All video platforms offer code snippets that can be easily integrated into your own website. This saves tedious website programming. Those who do not want the embedded videos to be financed by third-party advertising pay a small fee to remain ad-free. - Which software can I use to create my own videos?
Watch out, here comes advertising!!! There are various providers of good video editing software. The market leader in Germany is Magix with its Video Studio Deluxe. Cyberlink, Corel, Nero also offer good video editing software. We at bhv, have been dealing with the subject for years and have marketed Cyberlink, Corel and formerly Ulead in German-speaking countries. Since most programmes have become very complicated in the meantime, because the manufacturers add new features year after year, we recommend movavi Video Suite. The programme offers good templates, is easy to use, takes care of uploading to the major video platforms and includes cool features like shake-free action cam or drone shots.
The CERT-Bund, die Computer-Gefahrenstelle der Bundesverwaltung, is currently warning of an outbreak of the GandCrab encryption Trojan.
The sender of this e-mail is “Saskia Heyne” and the subject is “Bewerbung auf die angebotene Stelle”. Attached to this email is a Word document which, when opened, tries to persuade the user to activate macros.

Without this step, the Trojan cannot execute its malicious code.
Only open Word files containing macros if you have obtained them from a 100% trustworthy source.
A typical attack on the IT infrastructure of companies is carried out in 3 steps.
- Search for vulnerabilities
Attackers first look for vulnerabilities in the system. This can be unbiased emails to employees, e.g. an inconspicuous invoice email to the accounting department. Network printers with open ports, IoT devices with old firmware or even routers whose known vulnerabilities have not been closed. In addition, danger can come from websites that have already been infected with malicious code and whose operators do not have enough resources to constantly pay attention to the security of their own websites.
Once the malicious code has been installed on a device in the network, it spreads quickly so that by the time it is discovered on one device, e.g. by anti-virus software, it is already installed on enough other devices. In this first phase, nothing happens yet. The malware is merely the bridgehead for further attacks. It copies itself to more and more devices and thus obtains additional rights within the network. - Installing malware
After spreading in the network, the malware loads various tools, e.g. to spy out passwords or remotely control devices. Depending on the type of attack, a wide variety of software components can be loaded onto the compromised devices. Due to the malware’s already acquired “rights”, the download of malware is not recognised as a threat. - Enforcement
The execution of the attack on a corporate network can vary greatly. For example, principals of the attack may be interested in trade secrets and information. The data is usually compressed on the affected computers and then sent to an address outside the company network. Criminals can encrypt data carriers and only release them after payment. Some attacks aim to drain computer power and bandwidth to produce cryptocurrency, for example, or to carry out DOS attacks against other systems. One thing most attackers have in common is that they have a lot of patience. It can take a very long time for those affected to realise that their system has been compromised.
How can you protect yourself from such an attack scenario?
- Basic protection
Basic protection is provided by security solutions, e.g. from Symantec, GDATA or Bitdefender. There are client solutions for each individual computer or network solutions for all devices. The Bitdefender Box is such a network solution. It offers protection for all devices, e.g. surveillance cameras, laptops, tablets within a WLAN network. - Attentive employees
The best firewall or security software can only work if the employees or users adhere to certain rules. For example, no private data carriers or smartphones should be used within the network. Furthermore, attention should be paid when opening e-mail attachments. Even with known senders, malware could be hiding within the email, so users should not only check the alias name, but also the actual email address. - Back-ups secure business operationsComplete protection will not exist. Careless or malicious employees can put a company at risk. To ensure that business operations can continue in the event of an emergency, data backups are essential. This way, in the event of a network-wide attack, it is possible to restore to a backed-up recovery point and restore most of the data. Simple back-up solutions are offered by Windows, for example, but we recommend better and above all automatic back-ups from EaseUS.
Not at all! That doesn’t sound good, but it corresponds to reality. There is software, e.g. from the NSO Group from Israel, which is specialised in penetrating foreign systems. If a targeted attack is made on a specific device, no antivirus programme can defend itself against it. Antivirus scanners work with signatures of known malware. In the case of a new, as yet unknown attack scenario, they cannot prevent the attack because there is no signature for it in their database
This is where endpoint security comes in. If attackers succeed in getting onto their target’s system, the infected malware must be executed. Modern operating systems such as Windows 10 try to prevent this by so-called whitelisting. With whitelisting, only programmes and components that have previously been classified as “clean” by the user are executed. Whitelisting only works as long as an attack uses components that are not known to be harmless to get to the performance.
An advanced protection mode is the “Guarded Desktop”, which builds a “secure protective shell” around critical applications and prevents critical activities. These include, among others:
- Keylogging: the recording of keystrokes.
- Record screen activity.
- Changes to messages e.g. emails and messengers.
- Injecting malicious code into whitelisted databases and applications.
With the App-Protect software from Reddfort, users can protect themselves from targeted attacks. The application consists of two components, a sophisticated whitelist system and the Guarded Desktop. App-Protect is effective even if the virus scanner has been overcome by a potential attacker. App Protect simply prevents the start of executable files (EXE, MSI, BAT, etc.) and v the execution of e.g. macros from Office documents (DOC, XLS, etc.). It is still possible to start files such as videos, music, photos and Office documents from external USB drives. However, the execution of active elements, which in turn load malware, is reliably prevented.
The best way to use App-Protect is on a newly installed system to prevent possible malware from already being installed in the system and subsequently being “protected” by App-Protect.
The OKR leadership model, which is particularly popular with start-ups, is quickly explained and easy to understand (or so the theory goes). The company defines a mission (objectives) and then defines milestones or key results to achieve the company’s goal. Simple to explain, difficult to implement!
The difficulty for most young companies and start-ups is not to lose focus in the initial phase and not to be distracted from the goal while building up the learning curve.
We recommend a very good book on this topic that explains the path and implementation of OKR in a practical way using a fictitious start-up.
Yes, and even as a free open source programme – Scribus.
Scribus is a powerful DTP programme that is constantly being developed. It also offers a lot of templates that can be easily adapted to personal needs. For example, standard formats such as A4, A6 flyers, wrap or zigzag folds can be used directly. With the professional colour management, the finished layouts can be sent in CMYK colours to any print shop for further processing without any problems. Special colours can also be individually controlled with Scribus.
Scribus can be downloaded via the following link: https://www.scribus.net/downloads/
Don’t be put off by the English website, both the language for installation and the user interface are available in German.
For a quick start with Scribus we recommend the book “Scribus Desktop-Publishing – Das Einsteigerseminar“
Yes, because e-mails offer the same protection against “reading” as the good old postcard. If you want/need to send really confidential data, such as business data, by e-mail, you cannot avoid encryption. The following options are available to protect messages/documents.
Password-protected files:
You can of course put the data in a password-protected file and then attach it to the e-mail. The only thing is that it is not very convenient to use and confidential things written in the message can still be read. The password should at least be sent by another means (messenger, telephone, etc.) and not by e-mail.
PGP (Pretty Good Privacy)
PGP uses a so-called public key procedure in which there is a uniquely assigned key pair. PGP is based on the so-called Web of Trust, in which there is no central certification authority, but trust is managed by the users themselves. Setting this up is much more difficult and presents many users with major hurdles.
Yes, one of the best known is the open source programme “FreeCAD”.
With FreeCAD you can create both 2D and 3D drawings. It is customisable, scriptable and extensible. With its extensive features, it is suitable for hobbyists/makers, experienced CAD users and also educators.
For an introduction to FreeCAD we recommend our book: “FreeCAD – 2D/3D Konstruktion – Das Einsteigerseminar“.
The new wave of attacks is mainly directed against companies.
Managing directors/CEOs (names can be found in the imprint of a website), sales and marketing staff (usually also publicly visible) and employees from public administrations (e.g. financial administrations). They are the most frequent targets of this wave of attacks, but anyone else can be affected.
With WeTransfer, the attackers use a very well-known platform for sending e.g. presentations, catalogues or larger graphics and photos. WeTransfer is a cloud service that is mainly used by companies and freelancers. It is an ideal Trojan horse to penetrate a company network. The phishing email looks very authentic. The sender appears to be the cloud service “WeTransfer”, the link to the alleged download file also looks genuine. However, the link leads to another website where the victim’s email address is saved in the first step. With this, the attackers have already identified all the easy targets.
In the next step, the website transmits malicious code to the victim’s computer. A good web browser protection like Bitdefender or McAfee can help with this step. The security software blocks access to the website and warns of the possible dangers (see picture).
Beware of a new wave of attacks via phishing emails
We carried out a test with Windows 10’s own security protection “Windows Defender”. Unfortunately, Defender allowed the website to be accessed and thus we were at the mercy of spying.
How can users defend against such an attack?
- The e-mail client should only receive e-mails in text format, not in HTML format. In addition, the automatic reloading of external content (e.g. graphics) should be prevented. When loading graphics, for example, the attacker can pass on malicious code and knows who has opened his e-mail (the e-mail address is thus identified as a potential target). The e-mails may not look as nice in text format, but an attacker can no longer tell whether an e-mail has been opened or even read.
- A healthy distrust, even with known senders, is the best protection. Does the colleague from accounting really send a WeTransfer file? Probably not. Excel or PDF files do not need much storage space and would be sent directly. If the colleague from the marketing department sends a file via WeTransfer, there is a higher probability that the email will be opened. Before clicking on the link in the email, look at the link address in the bottom left-hand corner of the email client. If it does not say “https://wetransfer.com/download/….” it is probably a phishing e-mail.
- If 1 and 2 didn’t help and the email was opened in an unfocused moment, a good security solution like Bitdefender can help ward off an attack.
- If 1 – 3 did not help, it is still possible to restore the system to a restore point or make regular updates with EaseUS ToDo Back-up.
Conclusion:
It remains exciting and the attacks are becoming more and more sophisticated. In the past, we received phishing emails from unknown senders in poor German or English. Nowadays, they are from known senders with halfway comprehensible content in the subject line. Even if the e-mails are encrypted on the Internet, the header with the e-mail address is readable, because otherwise it would not be possible to forward them to the right recipient. This is where cyber criminals come in and grab the e-mail addresses of the sender and recipient. With a watchful eye, common sense and a good security solution, the user is protected against a known phishing attack.
Dolibarr ERP & CRM is a browser-based and easy-to-use software.
In the Dolibarr settings, the accuracy for rounding (decimal places) and the general behaviour for rounding amounts can be defined.
There are two different methods for calculating VAT. The column-wise (vertical) calculation or the row-wise (horizontal) calculation.
In the vertical calculation, the net total per tax rate is determined for the entire invoice and the VAT total is calculated from this In the horizontal calculation, the VAT is calculated for each individual item line, taking into account the respective tax rate
Both methods of calculation are legally permissible, but can lead to rounding differences in the case of decimal places.
Example:
Item 1:
Item price of 0.99 EUR + VAT 19% = gross price 1.18 EUR
Item 2
Item price of 0,99 EUR + VAT 19% = gross price 1,18 EUR
Position 3:
Item price of 0,99 EUR + VAT 19% = Gross price 1,18 EUR
Calculation: (0,99 EUR + 0,19 EUR) x 3 = 3,54 EUR
Depending on the selected calculation, this results in rounding differences of 0.01 EUR. To create invoices without rounding differences in Dolibarr, the following settings must be changed.
Start -> Settings -> Accuracy – Tolerance
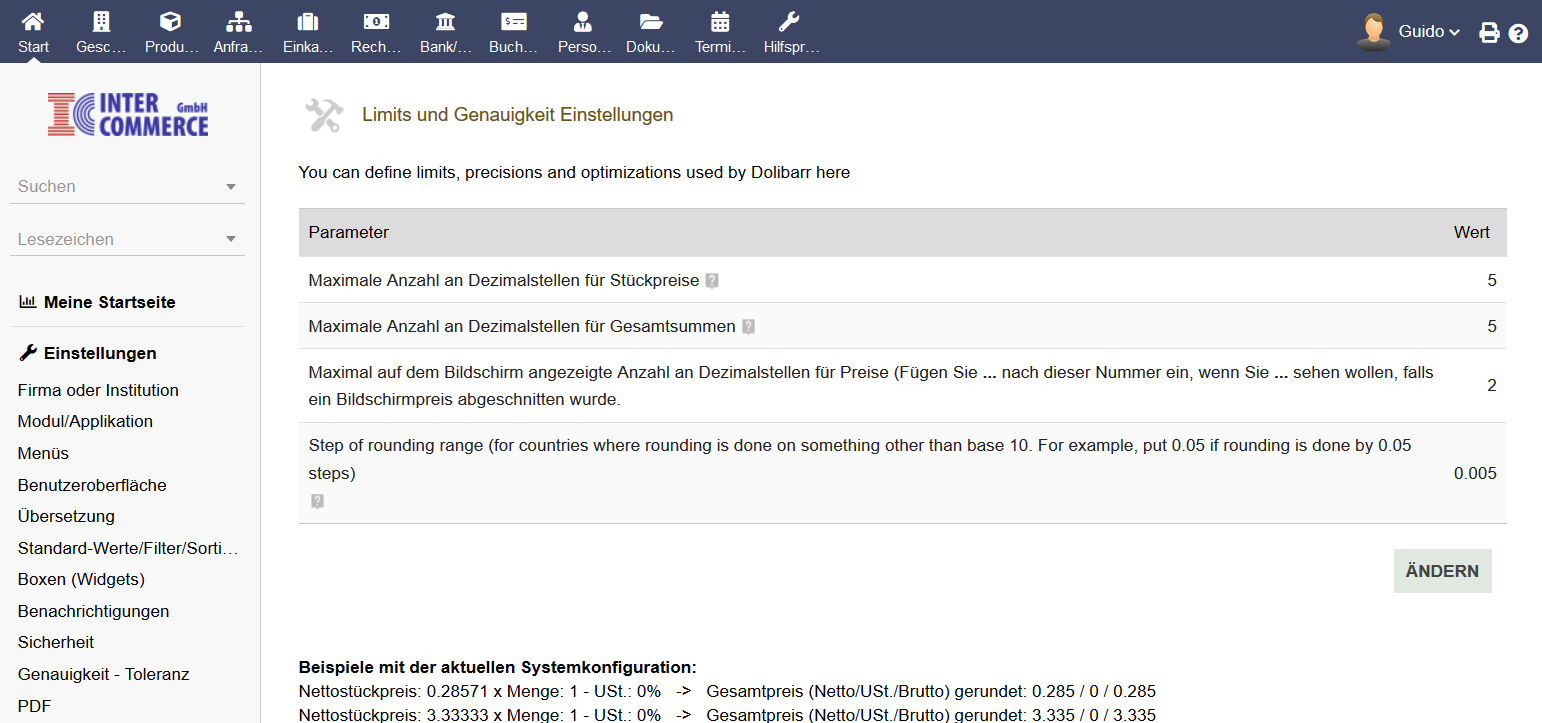
Maximum number of decimal places for totals = The number of decimal places for the total price.
Maximum number of decimal places displayed on the screen for prices … = The number of decimal places displayed on the screen.
Start -> Settings -> Advanced settings
Add the following entry as a new parameter:
“MAIN_ROUNDOFTOTAL_NOT_TOTALOFROUND” (Enter without quotes.)
… and set the value to “1” to activate it.












